5 Wireshark Filters
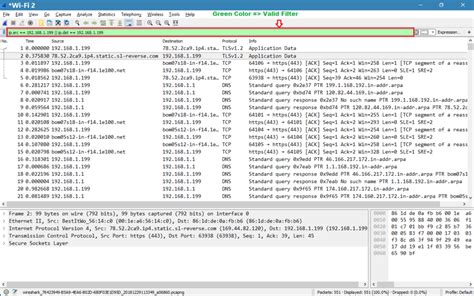
Introduction to Wireshark Filters
Wireshark is a powerful network protocol analyzer that can capture and display packets in real-time, helping network administrators and security professionals troubleshoot and analyze network traffic. One of the key features of Wireshark is its filtering capability, which allows users to narrow down the captured traffic to specific protocols, IP addresses, or other criteria. In this article, we will explore five essential Wireshark filters that can help you get the most out of your network analysis.
1. HTTP Filter
The HTTP filter is one of the most commonly used filters in Wireshark. It allows you to capture only HTTP traffic, which can be useful for analyzing web traffic, identifying potential security threats, or troubleshooting web application issues. To apply the HTTP filter, simply type “http” in the filter bar and press Enter. You can also use more specific filters, such as “http.request.method == GET” to capture only GET requests.
2. TCP Filter
The TCP filter is another essential filter in Wireshark. It allows you to capture only TCP traffic, which can be useful for analyzing TCP-based protocols such as FTP, SSH, or SMTP. To apply the TCP filter, simply type “tcp” in the filter bar and press Enter. You can also use more specific filters, such as “tcp.port == 80” to capture only traffic on port 80.
3. IP Filter
The IP filter allows you to capture traffic based on specific IP addresses or subnets. This can be useful for analyzing traffic to or from a specific server or network segment. To apply the IP filter, simply type “ip.addr ==
4. UDP Filter
The UDP filter allows you to capture only UDP traffic, which can be useful for analyzing UDP-based protocols such as DNS, DHCP, or VoIP. To apply the UDP filter, simply type “udp” in the filter bar and press Enter. You can also use more specific filters, such as “udp.port == 53” to capture only DNS traffic.
5. DNS Filter
The DNS filter allows you to capture only DNS traffic, which can be useful for analyzing DNS queries, identifying potential security threats, or troubleshooting DNS issues. To apply the DNS filter, simply type “dns” in the filter bar and press Enter. You can also use more specific filters, such as “dns.qry.type == A” to capture only DNS queries for A records.
📝 Note: These filters can be combined using logical operators such as "and", "or", and "not" to create more complex filters. For example, "http and tcp.port == 80" would capture only HTTP traffic on port 80.
Some key benefits of using Wireshark filters include: * Improved analysis efficiency: By narrowing down the captured traffic to specific protocols or IP addresses, you can quickly identify potential issues or security threats. * Reduced noise: Filters can help eliminate irrelevant traffic, making it easier to focus on the traffic that matters. * Enhanced troubleshooting: Filters can help you quickly identify the root cause of network issues, reducing downtime and improving overall network performance.
Here is a table summarizing the five Wireshark filters discussed in this article:
| Filter | Description |
|---|---|
| http | Capture only HTTP traffic |
| tcp | Capture only TCP traffic |
| ip.addr == |
Capture traffic based on specific IP addresses or subnets |
| udp | Capture only UDP traffic |
| dns | Capture only DNS traffic |
In summary, Wireshark filters are a powerful tool for network analysis and troubleshooting. By using the five filters discussed in this article, you can quickly and efficiently analyze network traffic, identify potential security threats, and troubleshoot network issues. Whether you’re a network administrator, security professional, or simply a curious user, Wireshark filters can help you get the most out of your network analysis.
What is Wireshark and what is it used for?
+
Wireshark is a network protocol analyzer that can capture and display packets in real-time, helping network administrators and security professionals troubleshoot and analyze network traffic.
How do I apply a filter in Wireshark?
+
To apply a filter in Wireshark, simply type the filter expression in the filter bar and press Enter. For example, typing “http” would capture only HTTP traffic.
Can I combine multiple filters in Wireshark?
+
Yes, you can combine multiple filters in Wireshark using logical operators such as “and”, “or”, and “not”. For example, “http and tcp.port == 80” would capture only HTTP traffic on port 80.